Scam Text Messages Sent by Trusted Senders
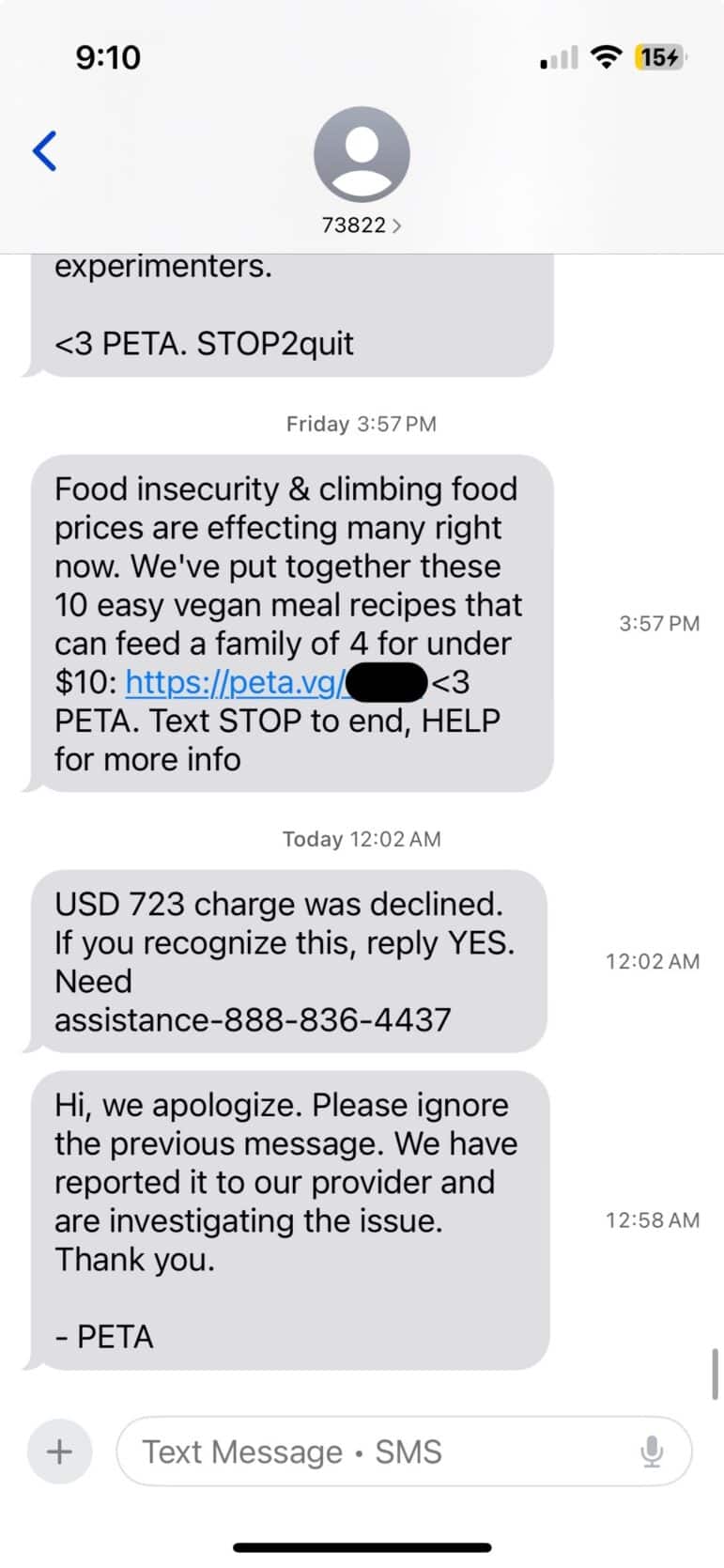
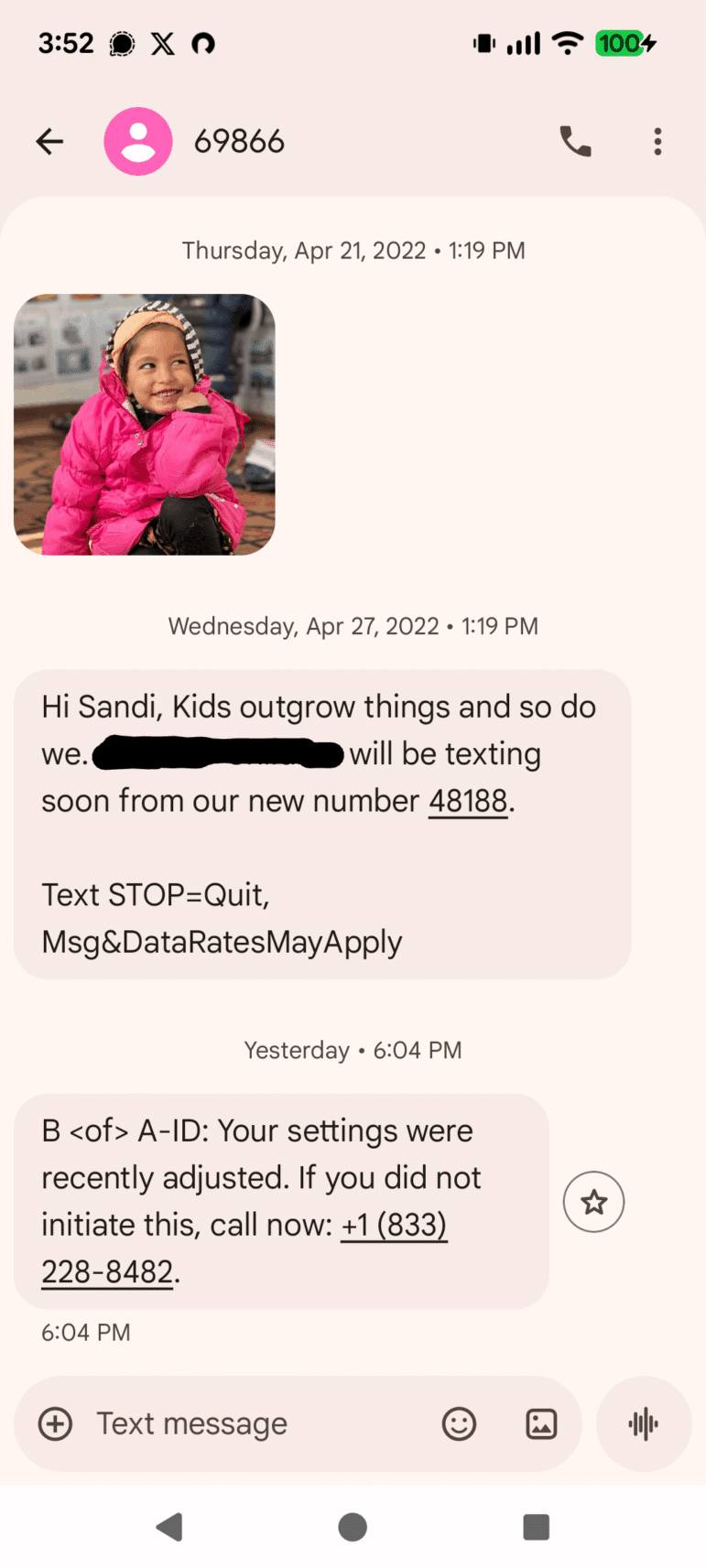
On a Monday evening, the bulk messaging platform Mobile Commons — which handles mass‐text alerts for organizations such as state agencies, charities, and political organizations — was compromised. An unauthorized actor gained access to the Mobile Commons platform and, over a roughly 4-hour period, used the service’s legitimate shortcode (five-digit number) texting system to send fraudulent messages. Recipients received scam text messages that appeared to come from organizations they subscribed to. The message would claim that a bank transaction (e.g., “$xxx.xx transaction denied”) had been attempted and, if the user didn’t recognize it, urge them to call a toll-free number. This number was controlled by the scammers.
The trusted source was key: because the texts were coming via a platform used by hundreds of nonprofits and political groups, they avoided the typical red flags of spam. The short codes involved are not only tightly regulated, but each organization is fully vetted before being assigned its unique five-digit number. This is why they are rarely flagged as spam.
Who Was Affected
Mobile subscribers to several kinds of organizations’ reportedly received the scam text messages: the state of New York (via their texting alerts), Catholic Relief Services, PETA, and Fight for a Union. On Thursday evening, I received a similar message from the old shortcode of a former Smart As A Fox client. This shortcode hasn’t been used by the client since 2022 and is now apparently a Mobile Commons test account. I also received the following alert after 7pm from Mobile Commons:
As of November 13th, 2025 at 19:28 Eastern Time, outgoing (broadcast) messaging is temporarily paused on the mCommons platform due to a recent security incident. Incoming messages and platform access remain available. Our team is working urgently with security partners to review and strengthen all safeguards. We’ll post updates here and notify you as soon as outgoing messaging resumes. For urgent questions, contact our support team.
While Mobile Commons told journalists that there is currently no proof that subscriber bank data was accessed, the fact that messages were distributed via trusted organizations is itself alarming.
Why This Matters
- Trusted channels exploited: Many people sign up with charities or political groups for legitimate alerts and expect the texts to be safe. Using those same channels gave the scam a veneer of credibility.
- Short-code legitimacy: Because the texts originated from properly registered short codes (via Mobile Commons and the Shortcode Registry), they bypassed common filters that catch spam or unknown senders.
- Social-engineering leveraged fear: The message used a familiar scenario — a “denied transaction” — to provoke a quick reaction, compelling recipients to call or respond without pausing to verify.
- Scale risk for nonprofits/political groups: Organizations that use bulk‐SMS services may be viewed as low-risk targets, but this event shows how they can be leveraged to reach many people quickly for further fraud.
How Organizations Can Protect Their Texting Programs from Future Breaches
Incidents like the Mobile Commons breach reveal just how vulnerable nonprofit and political messaging programs can be. These organizations often rely heavily on SMS to mobilize supporters, fundraise, and deliver critical updates — which makes them valuable targets. Strengthening security doesn’t just protect the organization; it protects every subscriber who trusts that those messages are legitimate.
1. Require Strong Authentication and Access Controls. Nonprofits should insist that their texting vendors support multi-factor authentication (MFA), role-based permissions, and restricted access to message-sending tools. Only essential staff should have the ability to launch or schedule texts.
2. Audit Vendor Security Regularly
Organizations should review their vendor’s security posture at least annually. If a vendor cannot answer basic security questions, that’s a red flag. This includes:
- Penetration-testing results
- SOC 2 or similar certifications
- Encryption practices
- Policies for monitoring unauthorized access
3. Monitor Outbound Messaging in Real-Time
Make sure multiple members of your organization’s staff are subscribed to your mobile program. Set internal alerts for unusual behavior — such as large batches sent at odd hours, unexpected message content, or messages outside your regular segment lists. Some SMS platforms offer real-time log access and anomaly detection; nonprofits should turn these on.
4. Prepare an Incident Response Plan
If a breach occurs, speed matters. Organizations should have a clear plan. This prevents confusion and minimizes harm.
- Decide who is notified internally.
- Immediately notify and coordinate with the mobile platform vendor
- How subscribers will be informed
- Ex. Send a message to your mobile list instructing subscribers to ignore the previous message, apologize, and explain the security breach.
- Determine the steps needed to stop outgoing messages.
5. Create a ‘Message Verification’ Protocol for Subscribers
Organizations can protect their audiences by educating them on what legitimate messages look like. A simple webpage, updated regularly, can reinforce this. For example:
- “We will never ask for financial info by text.”
- “We will not send bank-related alerts.”
- “Our official short code is XXXXX — verify before responding.”
6. Demand Higher Security Standards from SMS Vendors. The nonprofit sector often relies on legacy texting platforms. Organizations should pressure vendors to:
- Provide 2FA Logins
- Enforce API key rotation
- Implement suspicious-login alerts
- Add outbound-message approvals
- Provide transparent logs of all activity
This incident is a reminder: even communications from trusted groups can be hijacked, so it pays to treat any unexpected request—especially those involving money or sensitive information—with caution. Nonprofits may not control the technology, but they can demand safer infrastructure to prevent scam text messages like these from being sent out in the future.